Test Your Ransomware Detection System with a Powerful PowerShell Script
02//23
DISCLAIMER - The authors of this script do not recommend testing security scripts on a production environment. Doing so could cause serious damage to the system or environment. The authors of this script are not responsible for any damages caused by running this script on a production environment. It is the user’s responsibility to ensure that this script is only used in a safe and secure environment.
This script allows you to easily edit, open and close various files. This script is written using PowerShell, and it allows users to create a list of (Not so “Suspicious”) files to open, edit and close. The script creates a temporary directory, if it does not already exist, and it also creates a working folder for the generated files.
The script can open and close both .bat and .ps1 files, and it also checks if the files already exist before creating them. You can edit the files to create any file extension type. The goal is to make sure you test it with suspicious file types. It also utilizes the Windows Shell object to perform mouse movements. This allows the script to simulate user interaction with the mouse, which is a good way to see if your IDS creates a log for this kind of activity.
Overall, this script is a powerful and efficient way to simulates suspicious activity and get your antivirus or ransomware detection software to response appropriately. It is a great tool for automating security tasks, and it helps to improve cybersecurity productivity. It is a must-have for any user looking to streamline their workflow.

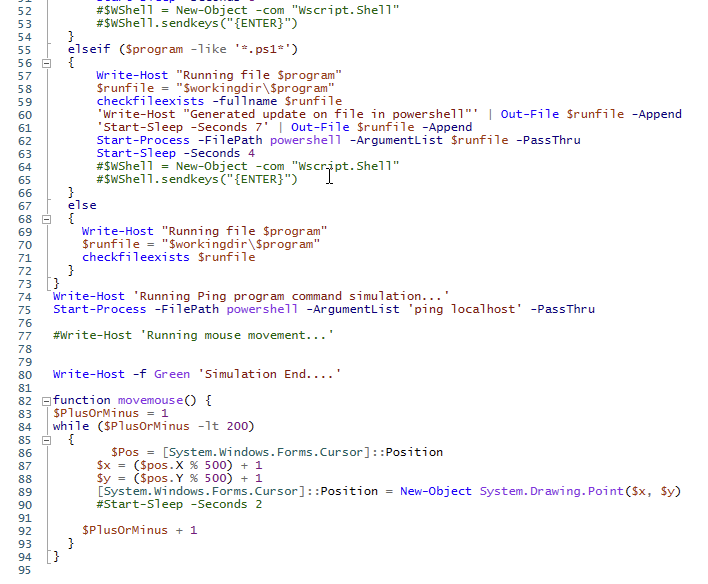
This creates a list of files (test1.txt, notepad.bat, notepad1.txt, notepad2.txt, notepad3.ps1, notepad4.bat) and stores them in a folder called "c:\Temp\working". It then runs a simulation where it checks if the files exist, creates them if they don't and updates them if they do. The script also runs a ping program command simulation and a move mouse function which moves the mouse cursor around the screen. The script is designed to demonstrate how files can be opened, edited and closed
This script allows you to easily edit, open and close various files. This script is written using PowerShell, and it allows users to create a list of (Not so “Suspicious”) files to open, edit and close. The script creates a temporary directory, if it does not already exist, and it also creates a working folder for the generated files.
The script can open and close both .bat and .ps1 files, and it also checks if the files already exist before creating them. You can edit the files to create any file extension type. The goal is to make sure you test it with suspicious file types. It also utilizes the Windows Shell object to perform mouse movements. This allows the script to simulate user interaction with the mouse, which is a good way to see if your IDS creates a log for this kind of activity.
Overall, this script is a powerful and efficient way to simulates suspicious activity and get your antivirus or ransomware detection software to response appropriately. It is a great tool for automating security tasks, and it helps to improve cybersecurity productivity. It is a must-have for any user looking to streamline their workflow.


This creates a list of files (test1.txt, notepad.bat, notepad1.txt, notepad2.txt, notepad3.ps1, notepad4.bat) and stores them in a folder called "c:\Temp\working". It then runs a simulation where it checks if the files exist, creates them if they don't and updates them if they do. The script also runs a ping program command simulation and a move mouse function which moves the mouse cursor around the screen. The script is designed to demonstrate how files can be opened, edited and closed

.png)